Cyber Premium
Comprehensive CyberSecurity services
for Small Businesses
As your business grows, so do the risks it faces. Cybercriminals are continually evolving their tactics to specifically target small businesses. In response, it’s crucial to implement robust security measures. The Cyber Premium package from CISO Online™ offers comprehensive, tailor-made security solutions designed to protect small businesses from these advanced threats.
Take your cybersecurity to the next level. Contact us to learn more about Cyber Premium.
Explore our Cyber Premium Package
to find the right fit for your organisation
Prevention is better than cure. Be proactive, not reactive!
Each package consists of two phases
Your CYBERSECURITY journey
SECURITY Uplift
phase 1
SECURITY Operation
phase 2
SECURITY Uplift
One-off Implementation Fee
This initial phase focuses on enhancing your cybersecurity posture and raising awareness. This phase is a one-time implementation effort, typically taking between 2 to 5 months to complete, depending on the chosen package.
SECURITY UPLIFT - Phase 1
Identity Protection
Logindetails and passwords
Advanced
Email Protection
Advanced
Advanced
Data Protection
Data Loss and Leakage
Standard
Internet Protection
Standard
User Behaviour Protection by AI
Advanced
Unified Security Operation Centre (SOC)
Advanced
Security Awareness Training
Advanced
Suitable for but not subject to
Small Businesses
with 1 to 250 users
SECURITY Operation
Ongoing Monthly Fee
Following the uplift, this phase centres on ongoing cybersecurity operations and defence. The objective is to maintain a secure environment and address your evolving security needs continuously. This phase involves a recurring monthly investment.
SECURITY operation - Phase 2
Ongoing User Behaviour
Analysis and Protection by Al
Advanced
Unified Security Operation Centre (SOC)
Proactive Response to Security Events,Vulnerability Remediation & Incident Response
Advanced
Advanced
CISO as a Service Advisory
Monthly
Login details, passwords and new users
Advanced
Advanced
Computers, Laptops, Smartphones and tablets
Advanced
Standard
Standard
Advanced
Suitable for but not subject to
Small Businesses
with 1 to 250 users
Explore our Cyber Premium Package
to find the right fit for your organisation
SECURITY UPLIFT in details
Phase 1

Next-Gen protection with adaptive AI security
Next-generation protection leveraging AI to catch and block all types of emerging threats. This rapid evolution underscores the need for agile and innovative security solutions using AI and machine learning models, behavior analysis, and heuristics.
How is this achieved?
- Behavior-based and real-time protection, which includes always-on scanning using file and process behavior monitoring and real-time protection.
- Detecting and blocking apps that are deemed unsafe, but might not be detected as malware.

Advanced protection of your identity, login details and credentials
Cyber Security starts with protecting your identity. Protecting your personal and business identity, preserving privacy, maintaining reputation, complying with Privacy ACT, andavoiding financial and legal consequences associated with identity theftand fraud.
How is this achieved?
- Dedicated Admin account and user accounts hardening.
- Multi Factor Authentication (MFA).
- Conditional Access Policies.
- Biometric Sign in.
- Password Protection.
- Self Service Password Reset.

Seamless login to business Apps using single sign on (Start with 3 Apps)
Use your protested M365 login across your business applications such as your accounting or CRM is accomplished by implementing Single Sign-On (SSO). This adds additional security and simplifies access. (3 business applications included).
How is this achieved?
- Implementing Seamless Single Sign-On (SSO).
- Securely access multiple applications by using Microsoft365 credentials.
- Leverage strong Microsoft 365 authentication methods for business applications, such as multi-factor authentication (MFA).

Work anywhere securely on any windows device
The concept of “Work any where securely on any device” refers to the ability to perform work tasks from any location using any device, while ensuring that data and systems remain secure. The Zero Trust security model is often implemented to protect such environments, as it does not automatically trust any environment.
How is this achieved?
- Roaming desktop for Windows machinbes.
- Providing users with a unified experience across their Windows. devices and reduces the time needed for configuring a new device.
- Setting up and pre-configure new devices, getting them ready for productive use.

Branded user login experience
M365 branding package involves personalising the Microsoft portal with your company’s branding. You can also present Terms of Use information to end users along with conditional Access policies to employees or guests before getting access.
How is this achieved?
- Customising images and text on the sign-in pages to create a consistent experience for users.
- Standard Terms of Use statements to employees or guests .
- Determine who has or hasn't accepted Terms of Use.

Advanced email protection against next-gen threats
Email protection is essential for defending againstphishing attacks, malwarethreats, Business Email Compromise (BEC) scams, maintaining business continuity, and preserving reputation and trust in today’sdigital environment.
How is this achieved?
- Anti-malware, Anti-spam and Anti-phishing policies .
- Safe attachments and Safe links.
- email authentication (DMARC, SPF, DKIM).
- Phishing report email quarantine.

Advanced computer & laptop protection against viruses, malware and ransomware
Protecting computers and laptops is essential for protecting data, defending against viruses & malware threats, ensuring business continuity in both personal and organisational contexts.
How is this achieved?
- Defender for Endpoint and Windows Security, providing Antivirus protection, continually update and scans for malware and viruses.
- Identify new malware and blocks it within seconds, offering rapid protection against emerging threats.
- Windows Firewall as a security feature that helps to protect your device by filtering network traffic that enters and exits your device.

Dedicated protection for company-issued and BYOD devices (Laptops, Smartphones, Tablets)
Device protection such as laptops, smartphones and tablets is essential for safeguarding Apps and protection for company data on any device preserving privacy, preventing identity theft, enabling remote device management.
How is this achieved?
- Device encryption.
- Mobile Device Management (MDM) policies.
- Mobile Application Management (MAM) policies.
- Remotely wipe lost or stolen devices.
- Secure and manage M365 apps (Outlook, Teams, OneDrive, Word, Excel, PowerPoint) on any devices.
- Protect organisational data on company provided and bring on your own (BYOD) devices.
- Mobile Defender and Antivirus for Android and iOS devices.

Data classification and standard data loss & leakage protection on any device
Data classification and sensitive data loss and leakage protection are crucial for safeguarding
sensitive information and preventing unauthorised access. By implementing data loss prevention (DLP) measures, you can reduce the risk of data breaches, regulatory fines, and reputational damage.
How is this achieved?
- Identify and classify sensitive information, such as personal data, your intellectual property (IP), or financial records, across your data estate.
- Classifying and labelling your documents and data (structured and unstructured for supported platforms).
- Define policies to control access to sensitive information and prevent unauthorised access and unauthorised change.
- Tracks the movement of sensitive information within the organisation.

Standard Website filtering
Website filtering is crucial for you to prevent access to malicious or inappropriate websites, enhancing network security whilst maintaining a more productive work environment.
How is this achieved?
- Users are blocked from accessing certain websites, categorised as restricted, regardless of their location.
- Access to detailed web reports from a single central location, providing in sights into both attempted and actual web accesses, enhancing visibility into web usage.

Shadow IT Repoprt (Cloud Apss visibility)
Shadow IT refers to the use of software, applications, and services available on the Internet without explicit approval or oversight from the IT department.
How is this achieved?
- Visibility into all cloud applications to obtain a comprehensive picture of cloud apps activity and enact securitymeasures accordingly.

Unified Security Operation Centre (SOC)
Having a Unified Security Operation Cnetre (SOC) including incident response and vulnerability remediation is a critical process, involving the identification and resolution of security vulnerabilities within your M365 environment. This includes addressing weaknesses that could be exploited bycyber threats in software, systems, or cloud.
How is this achieved?
- Identify, assess, remediate, and track all your biggest vulnerabilities across your most critical M365 assets, all in a single solution.
- Rapidly and continuously prioritises the biggest vulnerabilities on your most critical assets and provides security recommendations to mitigate risk.
- Proactive incident response as per SLA.

Advanced log collection
Regular advance log collection is required to detect and mitigate security incidents, enhancing overall cybersecurity resilience.
How is this achieved?
- M365 unified log collection and centeralised management of audit logs, which includes collecting and processing logs from various sources.
- Log ingestion into a SIEM platform is essential for threat detection,compliance, and security incident management.
- Archive logs for compliance purposes.

Security Awareness Training & Simulated Phishing
Human error is how most organisations get compromised and hackers are always looking for new ways to exploit vulnerabilities and this include humans! To keep your employees educated on the latest tactics we offer one (1) year of a computer-based cybersecurity awareness training (starts with 25 user) as well as our proactive simulated phishing attacks (incl. 25 free licenses)
How is this achieved?
- Baseline security awareness training
- Ongoing monthly videos followed by a quiz to test the users understanding
- Reminders of key lessons learnt from the animated video in the form of an infographic and poster
- Simulated Phishing emails that are tailored and customised to test your employees.
SECURITY opertion in details
Phase 2

Next-gen protection with adaptive AI security
Next-generation protection leveraging AI to catch and block all types of emerging threats. This rapid evolution underscores the need for agile and innovative security solutions using AI and machine learning models, behavior analysis, and heuristics.
How is this achieved?
- Behavior-based and real-time protection, which includes always-on scanning using file and process behavior monitoring and real-time protection.
- Detecting and blocking apps that are deemed unsafe, but might not be detected as malware.

Ongoing vulnerability remediation and Incident Response tosecurity events (threat hunting) - Advanced
Ongoing vulnerability remediation, incident response and proactive response to security events is acritical process, involving the identification and resolution of security vulnerabilities within your Microsoft cloud environment.
How is this achieved?
- Unified Security Operation Centre.
- Identify, assess, remediate, and track all your biggest vulnerabilitiesacross your most critical M365 assets, all in a single solution.
- Proactive Incident Response to security events and threat hunting.
- Ongoing Secure Score monitoring and improvement with adaptive AI security.
Ongoing Secure Score monitoring and improvement with adaptive AI security
Ongoing operation leveraging M365 portal capabilities to maintain and improve your secure score. In addition, a monthly Ongoing Security Report is essential for continuous monitoring of emerging threats, proactive risk management, and ensuring regulatory compliance.
How is this achieved?
- Ongoing Secure Score monitoring and improvement with adaptive AI security.
- Monthly security report Leveraging M365 portal capabilities to maintain and improve your security posture.

Advanced log collection
Ongoing log collection and providing monthly advanced security reports is required to detect and mitigate security incidents, enhancing overall cybersecurity resilience.
How is this achieved?
- M365 unified log collection and centeralised management of audit logs, which includes collecting and processing logs from various sources.
- Logs essential for threat detection, compliance, and security incident management.
- Archive logs for compliance purposes.

CISOaaS advisory and ongoing review of the policies - Monthly
Cyber security policies defined in your M365 environment are safeguarding your data and systems from cyber threats. They provide a strategic framework for protecting sensitive information, ensuring operational continuity, maintaining trust, and complying with legal standards. Updating M365 policies is critical for your security posture and overall success.
How is this achieved?
- Ongoing review of M365 policies by leveraging our CISO as a Service(CISOaaS) capabilities and experience - Monthly

Ongoing support for provisioning new users/licenses and updating user credentials
Cyber Security starts with protecting your identity. Ongoing protection of your business identity by provisioning new users/licenses and updating user credentials
How is this achieved?
- Ongoing Multi-Factor Authentication (MFA) support.
- Updating Conditional Access Policies.
- Ongoing Biometric Sign in support.
- Self Service Password Reset support.
- New users and licenses provisioning.

Providing seamless login for new users using single sign-on (SSO)
Providing seamless login for new users using single sign-on (SSO). New and current users will be using your protectedM365 login across your business applications such as your accounting or CRM.
How is this achieved?
- Implementing Seamless Single Sign-On (SSO) for new users
- Leverage strong Microsoft 365 authentication methods for business applications, such as multi-factor authentication (MFA).

Fine-tuning advanced email protection policies against the latest threat tactics
Fine-tuning advanced email protection policies against the latest threat tactics such as phishing attacks, malware threats, Business Email Compromise (BEC) scams is crucial for maintaining business continuity, and preserving reputation and trust in today’s digital environment.
How is this achieved?
- Updating and fine-tuning Anti-malware, Anti-spam, Anti-phishing policies, Safe attachments and Safe links.
- Ongoing assessment and release of quarantined email as per user request.

Fine-tuning advanced computer & laptop protection policies
Fine-tuning advanced computer &laptop protection policies are required for ongoing protection of computers and laptops are essential for protecting data, defending against viruses& malware threats, ensuringbusiness continuity in both personal and organisational contexts.
How is this achieved?
- Fine-tuning Defender for Endpoint policies and Windows Security,
- Fine-tuning windows Firewall rules

Updating device protection policies for new company-issued and BYOD devices (Laptops, Smartphones, Tablets)
Updating device protection policies for new company-issued and BYOD devices such as laptops, smartphones and tablets is essential for safeguarding Apps and protection for company data on any device preserving privacy, preventing identity theft, enabling remote device management.
How is this achieved?
- Fine-tuning and updating Mobile Device Management (MDM) policies.
- Fine-tuning and updating Mobile Application Management (MAM)policies
- Remotely wipe lost or stolen devices.
- Fine-tuning policies and managing M365 apps (Outlook, OneDrive, Word, Excel, PowerPoint) on any devices.
- Managing Mobile Defender and Antivirus for Android and iOS devices.

Ongoing review of dataloss& leakage protection policies
Ongoing review of data loss & leakage protection policies is crucial for safeguarding sensitive information and preventing unauthorised access. By updating data loss prevention (DLP) policies, you can reduce the risk of data breaches, regulatory fines, and reputational damage.
How is this achieved?
- Ongoing review and update of DLP policies to control access to sensitive information and prevent unauthorised access and unauthorised change.
- Tracks the movement of sensitive information within the organisation.

Ongoing review of website filtering
Ongoing review of website filtering is crucial to prevent access to malicious or inappropriate websites, enhancing network security whilst maintaining a more productive work environment
How is this achieved?
- Ongoing review and update of website filtering categories.

Ongoing Shadow IT Repoprt (Cloud Apss visibility)
Shadow IT refers to the use of software, applications, and services available on the Internet without explicit approval or oversight from the IT department.
How is this achieved?
- Visibility into all cloud applications to obtain a comprehensive picture of cloud apps activity and enact security measures accordingly.

Updating Security Awareness training plans and ongoing simulated phishing campaigns
Human error is how most organisations get compromised and hackers are always looking for new ways to exploit vulnerabilities and this include humans! Updating Security Awareness training plans and ongoing simulated phishing campaigns are required to keep your employees educated on the latest tactics.
How is this achieved?
- Ongoing quarterly Security Awareness training plans and ongoing simulated phishing campaigns
Ultimate Cybersecurity Solutions
for Maximum Protection
In the rapidly evolving digital landscape, businesses face sophisticated cyber threats that require robust protection. For organisations that prioritise security and demand the highest level of protection, our Cyber Premium package is the ultimate solution. This package not only includes all the features of the Cyber Essentials package but also extends security to an advanced level with several additional measures. With Cyber Premium, you receive a high standard of protection tailored to meet the unique demands of your business.
Ensure maximum protection for your business. Contact us to learn more about Cyber Premium.

ITS NOT A MATTER IF YOU FACE A CYBER ATTACK, IT'S WHEN!

In today’s digital landscape, Technology plays a critical role in nearly every aspect of your business, offering simple ways to collaborate with your team and engage with customers. and drive revenue. This ease of collaboration also increases the risk of cyberattacks. With the recent surge in remote work, the potential for both internal and external security breaches have significantly escalated, heightening the overall risk to your business.
Recognising the budget constraints faced by SMBs, our partnership with Microsoft as a Cloud Solution Provider (CSP), enables us to offer advanced and scalable cloud-based cyber security solutions and ongoing operations, so SMBs can focus on their core business rather than cyber security challenges.
We have designed Cyber Premium package tailored to meet the unique needs of small businesses. Our scalable solutions are crafted to fortify your digital environment, enhance your cybersecurity posture and behaviour, and establish a secure collaboration space, allowing you to focus on what you do best.
BE CYBER SMART, NOT
CYBER SORRY!
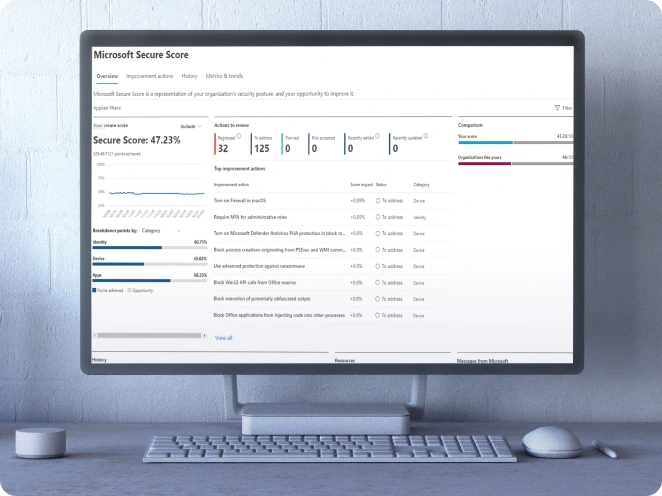
Secure Score is a measurement of your organisation’s security posture within your digital working environment. It is available for free in your Microsoft 365 tenancy under Microsoft Secure Score. Secure Score acts as a free penetration testing and vulnerability assessment tool, helping your organisation understand the safety of your collaboration environment. It provides an overview of your current risk level while working in a digital environment.

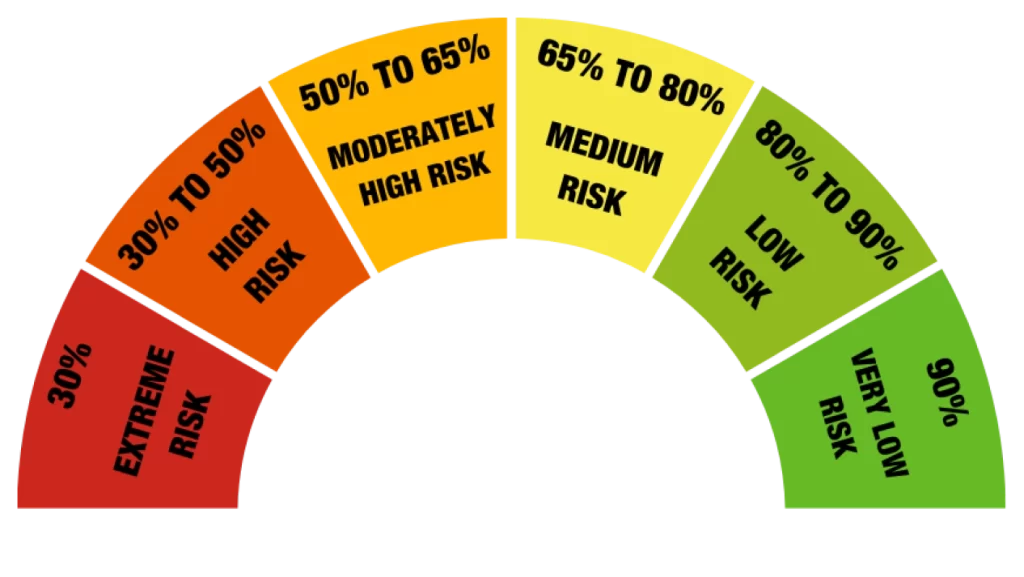
IMprove your Microsoft 365 secure score

- Extreme Risk: 30%
- High Risk: 30% to 50%
- Moderately High Risk: 50% to 69%
- Medium Risk: 65% to 80%
- Low Risk: 80 to 90%
- Very Low Risk: 90%
our cerfitcates
Our cybersecurity team is made up of highly skilled professionals, all certified by leading companies like Microsoft, CISCO, F5, Juniper, and IQS. They stay up to date with the latest industry standards and technologies to ensure your business is protected against the ever-evolving threats in the digital world. With our team on your side, you can trust that your cybersecurity is in expert hands.























our trusted partners








FAQ
ABOUT ‘’cyber premium’’
ciso online’s EXPERT ANSWERS
Why choose our SMB packages?
Understanding the unique cybersecurity needs and budget constraints of SMBs, we offer tailored packages that provide a solid baseline of protection. These packages are designed to ensure you receive the right coverage to safeguard your business while collaborating in a digital environment.
Our packages offer exceptional value for your money. We begin with a free security assessment, eliminating the need for costly penetration testing. Our pre-designed solutions further reduce expenses by removing the need for custom solution design, and our clearly defined deliverables ensure a cost-effective implementation.
Who are our Strategic partners delivering these packages?
Our strategic partnerships with ACSC (Australian Cyber Security Centre), Microsoft, KnowBe4, and NINJIO enable us to deliver comprehensive cybersecurity packages tailored to the needs of SMBs.
As a proud partner of the ACSC, we are trusted and supported by the Australian Government to help uplift the nation’s cybersecurity posture. Through this partnership, we contribute to Australia’s cyber defense and share our expertise, experience, skills, and capabilities with other security professionals. Our collective goal is to make Australian cyberspace secure for all users.
Our partnership with Microsoft as a Cloud Solution Provider (CSP) enables us to offer advanced and scalable cloud-based cybersecurity packages backed by the latest technologies and processes from Microsoft Cloud.
We also understand that cybersecurity is about more than just technology and processes; it’s about people. With over 85% of organisational breaches occurring due to human error, security awareness training is more crucial than ever. In collaboration with industry leaders KnowBe4 and NINJIO, we help protect your digital life by empowering you with the knowledge to establish a human firewall.
Who are our team delivering these packages?
Each package is delivered by a dedicated team of four professionals:
Principal Security Consultant: Provides strategic oversight and ensures that the security measures align with your business objectives.
Senior Security Consultant: Brings in-depth expertise and leads the technical implementation of advanced security solutions.
Security Engineer: Handles the technical execution, ensuring that all security features and configurations are effectively deployed and maintained.
Project Manager: Manages the project timeline, coordinates the team’s efforts, and ensures smooth communication with your organization.
Our team members are highly educated, hold the latest industry certifications, and bring extensive experience from working with large and high-end enterprises, applying this knowledge to benefit SMBs.
What are the phases in Cyber Premium?
Each package consists of two phases:
CISO Uplift: This initial phase focuses on enhancing your cybersecurity posture and raising awareness within your organisation. It is a one-time implementation effort.
CISO Operation: Following the uplift, this phase centres on ongoing cybersecurity operations and defence. The goal is to maintain a secure environment and continuously address your evolving security needs. This phase is optional if you have an in-house team capable of managing these operations.
How long does each phase take for Cyber Premium?
CISO Uplift: The uplift phase typically takes about 3 months to complete.
CISO Operation: The operation phase requires a recurring monthly investment and continues for as long as you need ongoing cybersecurity support.
What size businesses do we recommend Cyber Premium for?
What industries do we recommend our packages for?
What is the Cyber Premium package focused on protecting?
The Cyber Premium package is focused on essential cybersecurity measures, including:
Advanced Identity Protection: Cybersecurity begins with safeguarding your identity. Your login details and passwords (credentials) are your digital identity and must be properly protected in an advanced level.
Advanced Email Protection: Emails are a primary channel for communication and are often targeted in Business Email Compromise attacks. This package ensures your email system is secure in an advanced level.
Advanced Device Protection: This includes the advanced protection of your desktop computers, laptops, smartphones, and tablets—key tools for collaborating in digital environments.
Standard Data Protection: under the updated Privacy Act, SMBs are required to notify any individuals who are likely to be at risk of serious harm due to a data breach. Directors are held personally liable on data protection and unreported data breaches can lead to criminal record.
Standard Internet Protection: Browsing in internet can open your organisation to security risks and must be properly protected.
User behaviour protection by AI: Business users have normal behaviour type in the organisation aligned by their role. This need to be learnt by AI and flagged in a user doing an ubnormal behaviour if they’re compromised.
Advanced Vulnerability Remediation: As the digital landscape evolves, new vulnerabilities emerge. This package addresses the need to identify and mitigate these vulnerabilities regularly.
Advanced Security Awareness Training: With over 85% of organisational breaches occurring due to human error, security awareness training is crucial. This package provides essential training and simulated phishing attacks to help prevent such breaches.
Can I upgrade from one package to another?
What is included in the security awareness training?
What is the recommended computer for these packages?
What types of reports are included in the security log reports?
Can these packages help with compliance requirements?
How does AI-driven email security work?
What advanced endpoint protection features are included?
How does mobile device management (MDM) enhance security?
MDM enhances security by enforcing policies that control access to Microsoft 365 apps and organisational data on mobile devices. It includes features such as remote wiping of lost or stolen devices, conditional access policies, and protection for both company-issued and BYOD devices.
What is single sign-on (SSO) and how does it benefit my business?
Single sign-on (SSO) allows users to access multiple applications with one set of login credentials. It simplifies the login process, reduces password fatigue, and enhances security by reducing the risk of password-related attacks.




